Решение мобильной безопасности AnyOffice
Система унифицированного аудита техобслуживания HUAWEI (UMA) осуществляет централизованное управление, мониторинг и аудит деятельности всего персонала по эксплуатации и техобслуживанию (O&M) на предприятии, что позволяет снизить внутренние риски O&M сетевых устройств, серверов, баз данных и систем обслуживания для усовершенствования ИТ-систем управления предприятием. Кроме того, система UMA отвечает соответствующим правилам и стандартам аудита.
Background
In 2012, 20% of global employees brought their own mobile devices to work, such as the iPhone, iPad, or Android based devices. Along with huge IT consumption, Bring Your Own Device (BYOD) is gradually becoming the new norm. Originally thought to be just a trend concept, BYOD is now changing the way people work with quite an unstoppable momentum. With our own devices, we can exchange emails, conduct research and follow-up on potential sales opportunities more flexibly, promote information management over enterprise, flatten user interfaces, increase response times, and enhance decision-making efficiency. However, the openness of BYOD comes with enormous security and management risks. Therefore, is your enterprise ready for today's BYOD challenges?
Trend and Challenges
BYOD makes an office borderless. Users can simultaneously work and play Web games on the same mobile devices. Personal and office applications are crossing the boundary in between. For most enterprises, prohibiting the use of BYOD is just not practical. Majority of today's working staff (especially new entrants) are quite familiar with handling mobile technologies and have urged for BYOD support from enterprises. This need is forcing enterprises' IT management teams to not only adopts BYOD technologies but change the way they conduct business and operate in the workplace. At the same time, BYOD brings various problems and risks where an open and intelligent mobile platform leads to critical issues, including malicious code embedding, data leakage, mix of both personal and enterprise applications, and multiple platforms with different structures.
IT departments are finding themselves in a rather unsettling position where standards policies and configuration rules of the enterprise and those of the mobile devices are overlapping. Moreover, it is fairly difficult to graft security and management policies based on traditional PCs onto mobile devices, especially mobile devices belonging to employees. Enterprises must employ strategies for BYOD, including policy defining and management, and what mobile device to allow access to company information or levels of clearance.
Intelligent mobile devices function very much like PCs. However, they are completely without protection when accessing company information through web pages, downloading applications, or sending emails. So far, there are more than 20,000 types of malicious mobile software, 30% of which are Trojan horses, aiming to steal privacy and sensitive data. With the abuse of the root permission and the development of hack technologies, mobile devices are becoming the new hotbed for security-related risks. 71% of enterprises consider mobile devices, especially android devices, as a key security hazard.
Migrating enterprise applications to various mobile devices is a nightmare for IT departments. These challenges include: how to seamlessly and quickly transfer business to a mobile environment, how to avoid the high cost of in-house development, and how to cope with a highly complex mobile environment.
With the thriving use of mobile applications, enterprises are in short of corresponding management measures. Employees can download and install whatever application they want, which may reduce system availability, create huge security risks, or even disable the device.
Mobile devices are mostly of a small size and are prone to loss or theft. 47% of the companies interviewed say that large amounts of data are stored on mobile devices, including sensitive client information and classified data from emails. The loss of a single mobile office device not only indicates the potential leaking of confidential business information, but also possibly incurs law violations.
Overview of Huawei AnyOffice Mobile Security Solution
Targeting on the conflict between employee needs and company policy compliance, Huawei provides a balanced solution. The solution not only enables employees to access their company's intranet at any time, at any location, from any device, but also ensures strong security protection. Huawei is dedicated to providing an end-to-end mobile security solution and flexible application launching. Paying high regards to mobile device security, network transmission security, application security, sensitive data security, and security management, Huawei offers a unique balance between high efficiency and security of mobile office. Huawei provides a simple platform that supports the migration of all applications with excellent expandability and low cost to help companies cope with the complex mobilization.
Architecture and Key Components
Mobile security and management essentially resolve three issues: identity, privacy, and compliance. Focusing on these three key issues, Huawei provides enterprise clients with the most secure and user-friendly management solution in the industry today.
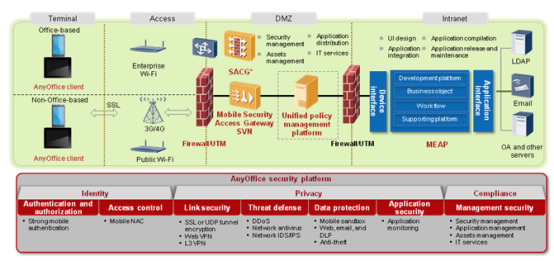
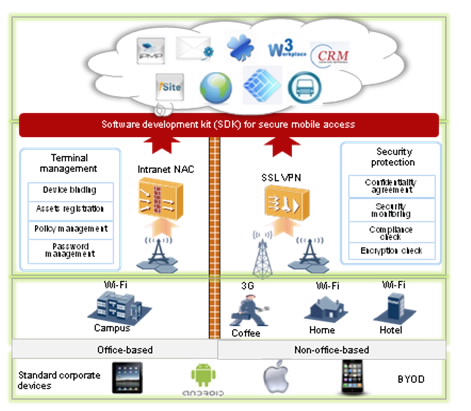
AnyOffice Intelligent Mobile Access Client
AnyOffice is the only mobile client that connects the user and the network/application. A simple client facilitates management and maintenance capabilities.
AnyOffice is a secure mobile office platform. In one-agent mode, it integrates a series of security applications, including security sandbox, security email client, security browser, MDM software, L3VPN client, and virtual desktop. This meets universal mobile office requirements and ensures secure, convenient, and efficient intranet access.
In addition, AnyOffice senses the access mode. With the interworking between the Security Access Control Gateway (SACG) of the company and the SVN, AnyOffice intelligently changes security policies based on user location (intranet or the Internet), offering a sound user experience.
Unified Access Control
AnyOffice can identify any device, user, location, time, and access mode through use of fine-grained access control. Enterprise IT staff can configure multiple policy templates for one user on the unified policy management platform and send them to AnyOffice. AnyOffice intelligently senses the network environment and triggers the corresponding security module. The security module works with SVN and SACG to implement precise network access control. From an airport lounge to the company's branch, users can use the mobile security access gateway (SVN) and then the Security Access Control Gateway (SACG) to access the company intranet. This whole process is transparent to users. AnyOffice therefore provides a simple and seamless user access experience.
Secure VPN Access
VPN mobile security access gateway SVN2000/5000 series is based on Huawei's high-availability hardware platform and employs dedicated real-time operating system. The gateway provides industry-leading performance, security, and availability, provides customers with flexible and controllable E2E link encryption, and ensures VPN access security.
Carrier-Class Mobile Threat Prevention
At the border of the enterprise network, Huawei carrier-class USG firewalls provide in-depth protection at the network side. The USG firewalls integrate Symantec's advanced intrusion prevention and anti-virus technologies, provide content security capabilities, including Anti-virus, IPS, Anti-DDoS, and content filtering.
Unified Security Policy Management
Huawei AnyOffice solution implements a unified and highly intuitive security policy management platform simplifying operations and management (O&M) and substantial IT cost savings. Security policies can vary with users, device types, locations, and time zones, therefore implementing fine-grained security access control.
Simple Enterprise Mobile Application Launching Platform
Enterprises are having difficulties in transplanting and launching mobile applications. Huawei Mobile Enterprise Application Platform (MEAP) moves enterprise applications smoothly by providing a more simple and easy integrated development environment and supporting various application types, such as HTML5, Native, or Hybrid, and realizes multi-platform launching per one development. This significantly simplifies the development process and tremendously lowers costs.
Products List
Typical Scenario of AnyOffice
Focusing on the requirements, features, and challenges of BYOD, Huawei BYOD mobile office security solution not only ensures that mobile office workers easily and securely access the enterprise intranet, but also provides excellent user experience.
Office-Based Scenario
In office-based scenario, unauthorized mobile devices have access to limited resources, including the DHCP server, SVN gateway, and RADIUS server. These resources are placed in the "pre-authorization zone". Authorized mobile devices, on the other hand, have access to the enterprise intranet resources, including the file server and Web server. These resources are placed in the authentication domain.
Figure 2-1 shows the networking diagram for the office-based scenario.
The SACG is deployed at the firewall side in off-line mode. The configured policy-based routing guarantees that all traffic destined to the authentication domain pass through the SACG first.
The SVN gateway is deployed at the firewall side in off-line mode and functions as a VPN access gateway. In the office-based scenario, the SVN and SACG interwork through Common Open Policy Service (COPS) to perform operations, including user permission policy delivery and user authentication.
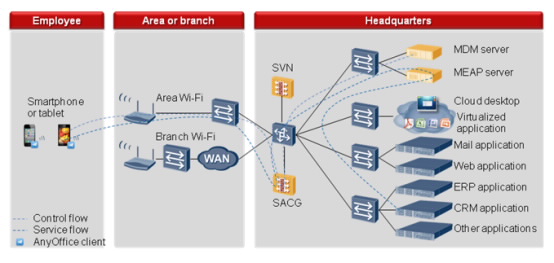
Office-based networking diagram
It takes two phases for a mobile terminal device to access an enterprise intranet. First, the terminal accesses the wireless network. Second, the terminal gets authenticated and authorized by the SVN and then accesses the enterprise intranet.
At the first phase:
The mobile terminal device establishes wireless connections with the Access Point (AP)/Access Control (AC).
The terminal gets authenticated by the AP/AC through 802.1X and establishes a TLS tunnel with the RADIUS server to protect the subsequent authentication packets. Before the 802.1X authentication succeeds, the AP/AC can transfer only authentication packets.
The RADIUS server authenticates the user information sent from the terminal device. If the authentication succeeds, the AP/AC permits the terminal device to access the DHCP server and the SVN gateway.
The AP/AC notifies the client of the successful authentication.
The terminal device has four handshakes with the AP/AC through the 802.11i protocol to negotiate the wireless communication key, securing the wireless communication.
The terminal device requests an IP address from the DHCP server.
In conclusion, at the first phase, the terminal device accesses the enterprise wireless network and obtains an IP address. The access user name and password are configured and delivered to terminal device by an IT administrator. The terminal device automatically sends the user name and password to the RADIUS server during authentication. In this process, an employee does not know the password, and a visitor of the employee needs an account from an enterprise employee.
At the second phase:
At the second phase, an enterprise employee and a visitor access the enterprise intranet in two different methods.
If an enterprise employee is not authenticated by the SVN yet, the employee needs to start the AnyOffice client on the mobile terminal. AnyOffice then displays the login page.
The employee enters the account and password.
AnyOffice establishes an HTTPS connection with the SVN and sends the employee ID to the SVN.
The SVN authenticates the employee ID and delivers the MDM access check policy to the AnyOffice client for further MDM check, including the password strength check, application compliance check, and jailbreak check.
AnyOffice reports the MDM access check result to the SVN gateway.
The SVN acknowledges the success of the MDM access check and instructs the SACG to permit the terminal device to access the authentication domain.
If an enterprise employee has started AnyOffice and passed the authentication, the process is as follows:
AnyOffice senses that the current network is the enterprise intranet.
AnyOffice attempts to reconnect to the SVN. Because of IP address changes, the original VPN connection between the Internet and the Intranet is interrupted.
The SVN authenticates the user and acknowledges the reconnection. Then the SVN instructs the SACG to permit the terminal device to access the authentication domain.
For visitors to the enterprise, because their terminal devices do not have AnyOffice, they use a web portal for the authentication. The process is as follows:
The visitor attempts to access the enterprise intranet through a browser. The HTTP traffic of the visitor first goes through the SACG. The SACG detects that the visitor is not permitted to access the authentication domain. Then the SACG acts as the destination IP address to establish a TCP connection with the terminal device, and sends an HTTP redirection packet to the terminal device to redirect it to the SVN.
The terminal device receives the HTTP redirection packet and then establishes an HTTPS connection with the SVN to access the portal authentication page.
The visitor enters the account and password on the portal page.
The SVN authenticates the visitor and instructs the SACG to permit the visitor's terminal to access the authentication domain. Usually, visitors' accesses are strictly controlled.
Non-Office-Based Scenario
When employees are out of the office, they connect to the SVN through AnyOffice, submit an account and password or a client certificate to establish a VPN tunnel with the SVN, and access enterprise intranet resources according to the granted permissions.
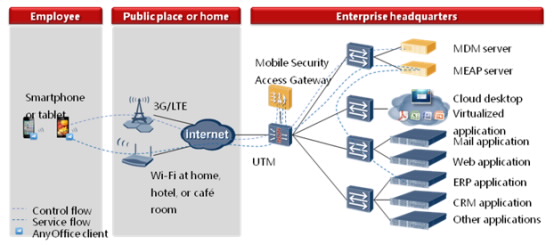
Non-Office-based networking diagram
Take email exchange as an example. After being authenticated and authorized by the SVN, mobile employees receive mails of the AnyOffice security mail client. AnyOffice encapsulates and encrypts mail requesting packets and sends them to the SVN through the SSL tunnel. The SVN decrypts, decapsulates, and injects the packets back to the USG. The USG inspects the packets for potential threats, including viruses, intrusions, and DDoS application-layer attacks, and then sends the clean traffic to the enterprise intranet.
Correspondingly, when the intranet mail server sends packets back to the USG, the USG inspects and filters the packets, and sends the packets to the SVN for VPN encapsulation and encryption. Then, packets are sent to AnyOffice through the SSL tunnel, decapsulated and decrypted, saved on the terminal device by a local encryption algorithm.
If a user operates files on AnyOffice, including downloading documents from the intranet and opening an encrypted file that is saved on AnyOffice, AnyOffice requests keys from the SVN for encrypting or decrypting the file.
Deployment Cases of AnyOffice
Mobile Working Project of a Large Enterprise in China
Challenges
1.E-flows cannot be submitted or approved when supervisors or employees are going on a business trip; documents are not immediately available when a Statement of Compliance (SOC) needs to be immediately prepared at the customer's site; documents that in urgent need are unavailable at the customers' sites.
2.Mobile security risks and worries are the biggest obstacle before the implementation of the mobile working project.
Solutions
1.Provide employees with standard device or BYOD for push mail service, e-flow processing, and eSpace instant communication.
2.Provide a complete mobile security and security management solution covering devices, networks, data, applications, and management.
3.Deploy a mobile sandbox system to ensure that enterprise data is isolated from personal data and meet data confidentiality requirements. In addition, provide an MDM solution to manage mobile device assets, applications, and data.
Value to the Customer
1.The solution adheres to the idea of anywhere, any time, and any device and improves productivity of managers by 9.4% and that of service representatives by 12.5%.
2.The solution ensures high security and balances corporate security policies and office administration efficiency.
3.The solution features simple and easy-to-use MDM and integrates with traditional endpoint management, greatly reducing management complexity and lowering costs.
Mobile Maintenance of a Large Energy Supplier
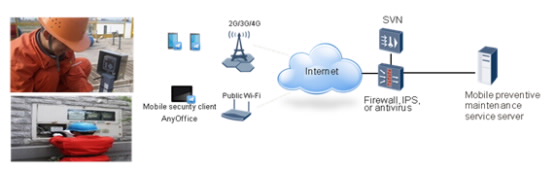
Challenges
1.Employees need to manually record device status data or faults during preventive maintenance, and then return to their offices to enter the collected data into the system. This involves a huge workload, which is time-consuming and brings about possible errors and mistakes.
2.Manually recorded information must also be stored. This involves more manpower resources to process the information and results in a high cost.
Solutions
1.Provide employees with tablets or smart devices, and install the mobile security client AnyOffice and professional mobile preventive maintenance software on the pads or smartphones.
2.Deploy a firewall, SVN gateway, MDM platform, and mobile preventive maintenance system in the information center.
3.Ensure that employees perform operations by using mobile terminals to collect and upload device status data in real time or report faults.
Value to the Customer
1.The solution supports more than 2000 employees for preventive maintenance.
2.The solution greatly improves service processing efficiency, making possible real-time information collection and fault reporting.
3.The solution greatly saves the workload required to record and transfer plenty of information, and therefore saves costs.
-
Продукты&Решения
- Все продукты
- Все решения
-
Как купить
- Свяжитесь с реселлером
- Отправьте свои требования
-
Стать партнером
- Стать партнером
- Регистрация на квалификацию партнера
-
Принять участие в обучении
- Запрос на сертификацию
- Запрос авторизованного партнера по обуению
- Академия Huawei онлайн
-
О нас
- Huawei Enterprise
- События
Copyright © Huawei Technologies Co., Ltd. 1998-2015. All rights reserved.
Условия использования|Политика конфиденциальности|Карта Сайта|Связаться с нами
