Solución de seguridad de información de empresa
Information technology is changing quickly, especially in the realm of new technologies and business models such as Bring Your Own Device (BYOD), Cloud computing and big data, which improve collaboration efficiency and enable sustainable business development.
Information technology is changing quickly, especially in the realm of new technologies and business models such as Bring Your Own Device (BYOD), Cloud computing and big data, which improve collaboration efficiency and enable sustainable business development.
With the proliferation of enterprise information technology, data security problems loom even larger. A substantial number of enterprises suffer from information security threats each year. According to statistics, 819 data leakage events and $20 billion in revenue losses were registered in 2011. Network attacks caused worldwide enterprise losses of $111 billion. For Chinese enterprises, 63.6 percent of business users fall into the "high risk" level each year due to network leaks, causing economic losses of up to $1 billion.
Companies must deal with the following information security problems:
- Security Management: Too many network devices and isolation of all security events create difficulties in analyzing and making decisions to avoid security risks.
- Data Leakage: Code, technology solutions, financial data, and business strategies are increasingly valuable but also can be leaked easily through copying, printing, outgoing email, and photography. For the top 1,000 Fortune companies, each data breach can represent $500,000 in losses.
- Network Attacks: The enterprise network is more complex than ever and, without protection, office terminals, networks, and servers are vulnerable to attack.
- IT Privilege abuse: IT operations staff and some services management staff can easily access the core services system and leak confidential data.
To deal with the challenges of information security, all companies must build a security system that encompasses both management and technology. An enterprise information security system should include security policies, security Operation and Maintenance (O&M), security organization, security capabilities, and security technology.
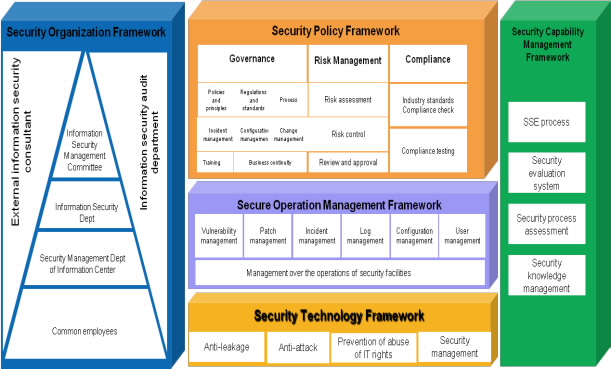
A Huawei information security solution has four sub-solutions: anti-data leakage, anti-attack, anti-IT privileges, and security management. The information security technology framework is illustrated in the diagram below:
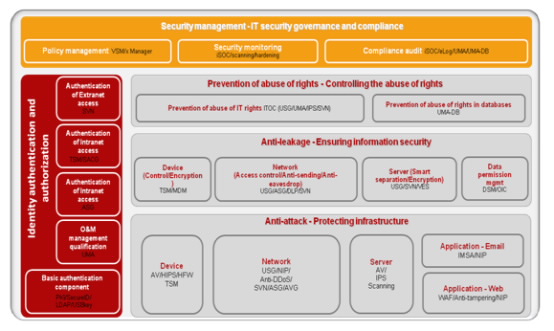
Anti-Data Leakage Solution
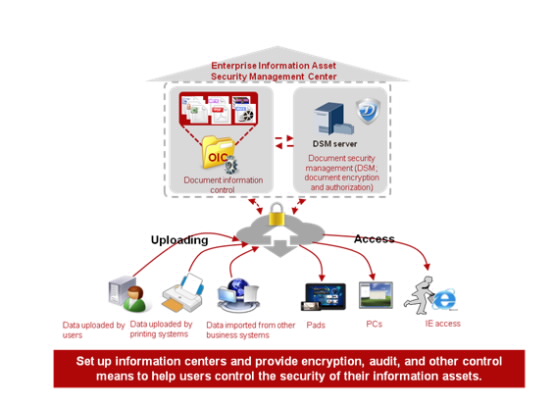
Enterprise Information Assets Management Solution
The information assets management solution helps enterprises safeguard all information assets and prevents confidential data from being leaked. This
solution comprises an Online Information Control Center (OIC) and Document Security Management (DSM) to provide centralized information assets management, access control, encryption control, tracking management, etc.
Anti-Terminal Leakage
The anti-terminal leakage solution prevents confidential data leaks from terminals via terminal ports control, document encryption, and terminal vulnerabilities repair. The Terminal Security Management (TSM) server controls terminal ports to prevent data leaks via USB copy. The Document Security Management (DSM) server enables document encryption and avoids data leaks via printing and snapshots.
Anti-Network Leakage
- Data transmission encryption: Data transmission between headquarters and branches or partners is encrypted via IPSec VPN. SSL VPN is adopted for BYOD.
- Data-zoning protection: The enterprise intranet is separated into logical areas to secure data.
- Out-going data control: Data going out via the Internet or email is checked and audited.
Solution Highlights
- Comprehensive terminal data protection covers terminal ports control, illegal external connection control, USB storage encryption, and BYOD data protection.
- Agile VPN solution (IPSec VPN and SSL VPN) secures data transmissions.
- Supports control of out-going data, including data size, data type, and highly sensitive data.
Anti-attack Solution
Anti-Terminal Attack
Terminal attacks can be avoided in two ways:
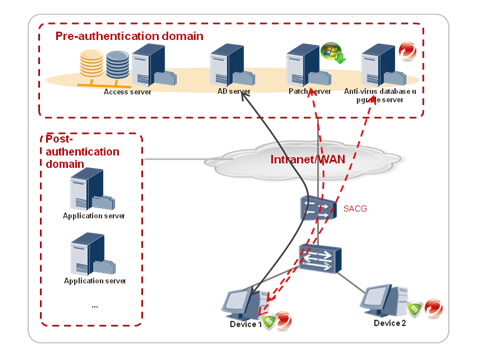
Terminal access control — Access policies are customized for terminals to prevent illegal access, separate non-compliant terminals, and authorize terminals to access different resources.
Terminal security hardening — Fix vulnerabilities, install patches, and upgrade anti-virus databases, all with one click.
Anti-Network Attack
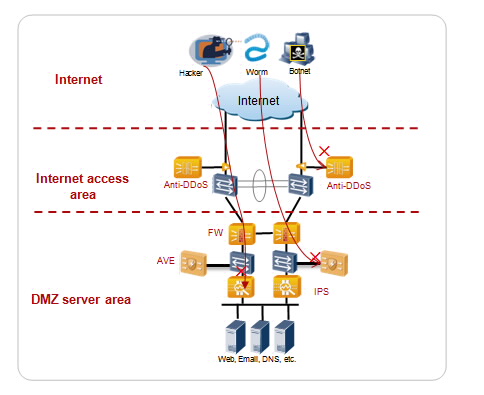
Anti-DDoS products are deployed to prevent Distributed Denial of Service (DDoS) attacks, and anti-virus and Intrusion Prevent System (IPS) firewall security products strengthen the enterprise security network to help thwart viruses and hackers.
Anti-Server attack
Four protection levels are adopted to prevent attacks on servers, including network protection, host protection, vulnerability management, and attack warnings.
- Network Protection: Anti-DDoS + Firewall + IPS + Anti-Virus
- Attack Warning: Host logs + security events + attack detection => correlation analysis => attack event =>warning
- Server Protection:
- Host firewall: Blocks illegal network connection and access.
- Anti-virus: Prevents virus, malware, and spam from damaging servers.
- Host IPS: Virtual patches for server
- Vulnerability management: Vulnerability scanning + configuration check + patch updates
Anti-Application Attack
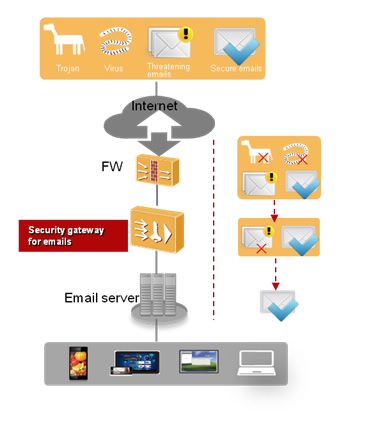
Application anti-attack solutions focus on Web and email.
Web:
- DDoS traffic cleaning
- Deploying IPS to prevent network attacks
- Deploying anti-page tampering systems to protect web pages
Email:
- Anti-spam
- Anti-virus
- Anti-attack
- Anti-fishing
- Content filtering
Solution Highlights
- Check security status, fix vulnerabilities and upgrade patches and anti-virus databases, all via one click.
- Leading anti-DDoS solution with the fastest attack response in the industry and 99.9999 percent reliability.
- Supports comprehensive attack detection for servers, terminals, web, and malware.
- Multi-level protection for servers: Network protection + host protection + vulnerability management + attack warning.
Anti-IT Privilege Abuse
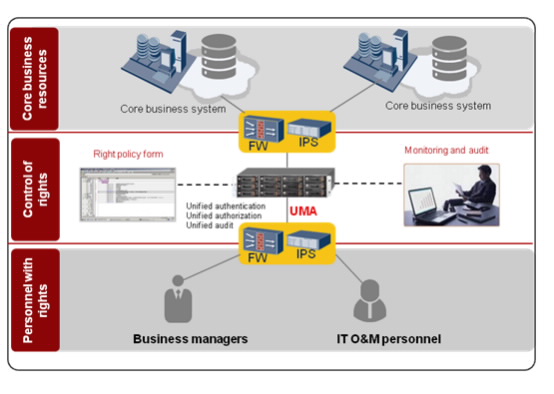
With information-based construction, many companies face ever-increasing difficulties operating and managing multiple IT systems. Multiple IT system access routes and inefficient account management mean a variety of IT operations staff can access systems and obtain confidential data.
The Huawei Unified Maintain Auditing (UMA) solution supports unified system entry and IT account centralization. All accounts and staff are matched exactly and all privilege abuse events are audited and tracked.
Solution Highlights
- Efficiently prevents IT operations staff from accessing the system server and using privileges to leak data.
- Supports tracking of system logging, operations, etc., for auditing purposes.
Information Security Management
Security Policy Management
The security policy management platform can manage all devices and apply security policies to all devices at once.

Security Operation Management
The Huawei Information Security Operations Center (ISOC) platform supports security event analysis, security risk warnings, security, security operations, and compliance audit management.
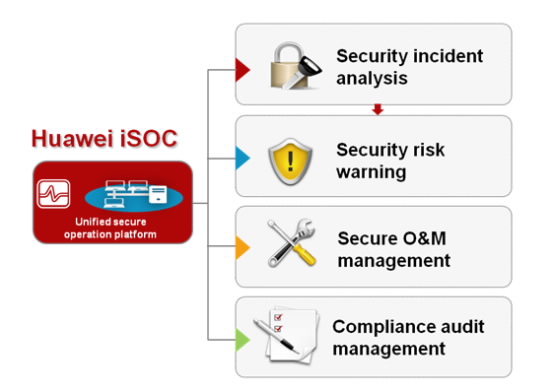
Solution Highlights
- Security policy is configured and applied visually via a batch file.
- Tracking logs can be collected and identified for 160-plus devices.
- A strong correlation analysis engine supports intelligent analysis of log events to achieve early warning for security incidents and post-hoc analysis.
FAW-Volkswagen Project
A large number of devices were scattered, and visitors and noncompliant devices could access the customer's network. Anti-virus and patching measures were difficult to perform. Peripheral components were not centrally managed, and office behaviors could not be collectively monitored. All of these issues endangered Intranet security.
Huawei Solution
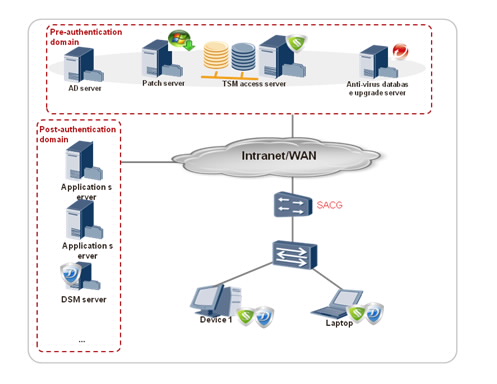
- Installed Terminal Security Management (TSM) agents on all access devices.
- Deployed two Security Access Control Gateways (SACGs) next to aggregation switches for the headquarters and branches to provide redundancy.
- Deployed a TSM system management server (provides redundancy) at headquarters' existing business systems area and deployed TSM System Control (SC) servers in headquarters and branches (two for each unit to provide redundancy)
- On the TSM system management interface, used the access control function based on the AD domain system.
- Core switches on the boundaries of branches support policy-based routing or port redirection, so that default routers can be automatically activated to allow access to all users when both the active and standby SM and SC systems are malfunctioning.
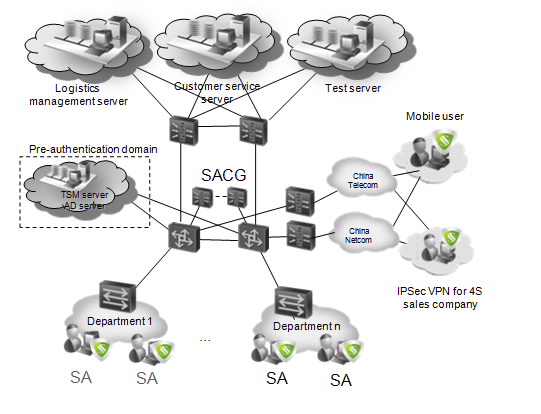
Customer Benefits
- Access via devices in a complex Intranet environment can effectively be controlled to minimize data leakage risks and virus infections, enhancing office efficiency and ensuring compliance with IT management regulations.
- Enables quick project construction, low investment, easy maintenance, and low operation and maintenance costs.
