Agile Controller
El Agile Controller es un sistema de control automático de recursos de red basado en aplicaciones y en el usuario que ha sido desarrollado por Huawei. Como componente central de las redes de área de campus inteligentes, el Agile Controller asigna de forma dinámica recursos de red y de seguridad en toda la red de área de campus, de acuerdo con un control centralizado de conceptos de SDN, lo que permite a las redes ser más ágiles en lo que respecta a la provisión de servicios.
Service Experience-Centric Network Redefinition
The network transfers attentions from technology, device, connectivity to user, service, experience. Originally, manual configurations are mainly performed. Currently, network and services can be dynamically deployed using natural language.
- Agile Controller dynamically allocates network and security resources on the entire campus network based on centralized control of software-defined networking (SDN) concepts, allowing resources to migrate with users and implementing free mobility.
- Agile Controller implements user-based QoS scheduling to preferentially forward data from VIP users in the case of limited network resources, ensuring good service experience of VIP users.
- Agile Controller allows users to use natural language to plan, deploy, and synchronize network-wide policies through one-click. Users do not need to focus on differences among various types of devices.
- Agile Controller can flexibly adjust network-wide rights, QoS and security policies to shorten service provisioning or network expansion durations, meeting fast service changing requirements.
All-Round United Security
Single-point protection is transferred to network-wide protection.
- Agile Controller collects logs from network devices, security devices, and service systems in a unified manner and uses Big Data correlation analysis to detect attacks and threats that can hardly be detected using single-node analysis.
- Agile Controller provides a virtualized security resource center to block or direct user traffic through intelligent linkage, actively defending against network attacks.
- Agile Controller provides comprehensive terminal security, desktop management, and mobile storage device management functions and predefines more than 5,000 terminal security policies, ensuring terminal access security.
Openness and Collaboration
Closed system is transferred to open system.
- Agile Controller provides northbound interfaces to interconnect with existing devices and service systems, improving service provisioning efficiency.
- Agile Controller provides southbound interfaces to integrate third-party terminal detection and event collection capabilities, building all-round united security systems.
Agile Controller has no special networking requirements except that there are reachable routes between the physical server where Agile Controller locates and network devices. Generally, Agile Controller is deployed in the data center.
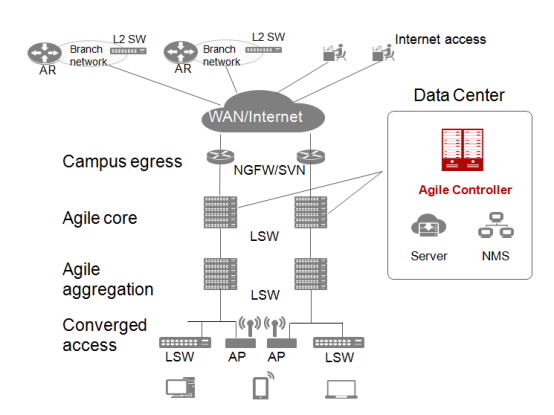
Agile Controller can be deployed on service manager (SM) and service controller (SC) servers to provide access control, visitor management, free mobility, and service orchestration functions, and on the Security View and iRadar server to provide the united security function.
| Configuration Requirement | SM&SC Server | SV&iRadar Server |
|---|---|---|
| CPU | 2 x 6-core processors, 2 GHz | 2 x 6-core processors, 2 GHz |
| Memory | 16 GB | 32 GB to 64 GB |
| Storage | 600 GB | 4 TB and above |

