Protecting the Internet egress against security threats from the Internet,
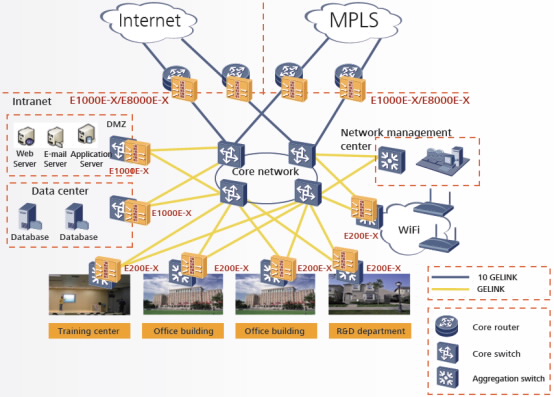
Protecting the Demilitarized Zone (DMZ) that is vulnerable to external attacks,
Protecting the data center that carries critical service data for enterprises.
Challenges
- Protecting the Internet egress against security threats from the Internet
- Protecting the Demilitarized Zone (DMZ) that is vulnerable to external attacks
- Protecting the data center that carries critical service data for enterprises
- Setting up a secure access edge between various service departments to prevent viruses from spreading
- Monitoring all internal terminals while reducing network risks
- Building secure communication channels between an enterprise’s headquarters and its branches
Advantages
Internet Egress Security
- High performance (a maximum of 200 Gbit/s throughput) that secures the Internet egress
- Highest virtual private network (VPN) performance and capacity that ensures consistent access to the VPN
- Excellent scalability that facilitates service expansion
- Flexible device deployment and assembled product modules
Security Zone Isolation
- Prevents the spread of security threats within an enterprise.
- Secures enterprise information by creating isolated security zones (such as OA office building and R&D department).
- Enhances security within an enterprise by protecting critical data and areas that are vulnerable to attacks.
Network Real-time Intrusion Defense
- Provides a powerful virus detection engine.
- Supports powerful event management and statistical analysis functions.
- Adopts virtual engine technology, allowing the deployment of detection rules to take effect in different areas.
- Provides a complete library and professional security solution team.
Antivirus
- Detects viruses embedded in files.
- Creates a simulated environment to remove viruses in advance.
- Proven high detection rate (99%).
- Enables a signature to cover tens of thousands of virus variations through a static heuristic engine.
- Publishes a new script engine on the antivirus engine within hours.
User Action Management
- Improves work efficiency.
- Reduces campus network risks.
- Reduces legal risks.
Unified Security Management
- Provides various services, such as Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) services.
- Supports the management and policy delivery of security devices, switches and routing devices.
- Supports customized development, enabling the management of logs of all devices, databases, servers and hosts in the live network.
- Provides various service report analysis.
- Reduces network operation and maintenance (O&M) costs.
- Retains the original user network typologies and devices to ensure network performance and reliability.
- Intuitive GUIs for better user experience.
- Flexible configuration of security policies and reports.
- Updated security policies and reports using the cloud knowledge base.
- Secure and reliable network operation using service continuity design and a real-time intelligent security monitoring platform.

