Controlador de acceso AC6605
El controlador de acceso AC6605-26-PWR de Huawei integra la funcionalidad switch Ethernet de 1000 M tanto para el control de acceso alámbrico como inalámbrico. El AC6605-26-PWR ofrece a los usuarios una amplia flexibilidad para la configuración de puntos de acceso (AP). Utilizado junto con los AP de la serie premium de Huawei, los AP de la serie mejorada de Huawei y los AP de la serie estándar de Huawei, el AC6605-26-PWR ofrece una solución de networking a nivel empresa para redes de campus, redes industriales y redes empresariales de pequeña y mediana escala. Además, extiende la cobertura del área de acceso inalámbrico.
Appearance
Ports
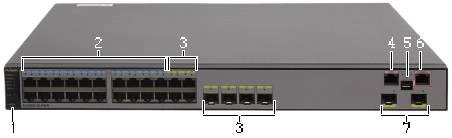
1. MODE button, switches working mode of indicators.
2. 20 10/100/1000BASE-T Ethernet electrical ports
Support 10M/100M/1000M auto-sensing.
Support PoE power supply on 20 ports.
3. Four combo ports
Support 10M/100M/1000M auto-sensing.
Support PoE power supply on four ports.
4. One ETH management port
5. One Mini USB port
6. One Console port
7. Two 10GE SFP+ uplink optical ports
Indicator Description

| Mode | Description |
|---|---|
| STAT mode | Steady green: A link has been established to the interface. |
| Blinks green: The interface is sending or receiving data. | |
| Off: No link has been established to the interface or the interface has been shut down. | |
| SPED mode | Steady green: 10M/100M/1000M interface: The interface is operating at 10/100 Mbit/s. 1000M/10G interface: The interface is operating at 1000 Mbit/s. |
| Blinks green: 10M/100M/1000M interface: The interface is operating at 1000 Mbit/s. 1000M/10G interface: The interface is operating at 10 Gbit/s. | |
| Off: No link has been established to the interface or the interface has been shut down. | |
| PoE mode | Steady green: The interface is providing PoE power. |
| The interface cannot provide PoE power due to any of the following reasons: The power of the PD exceeds the power supply capability of the interface or exceeds the threshold. The overall output power has reached the maximum output capability of the device. The PoE power function is not enabled on the interface in manual power-management mode. | |
| Blinks orange: The interface stops providing PoE power to a PD because a fault occurs (for example, an incompatible PD is connected to the interface). | |
| Steady orange: The PoE function is disabled on the interface. | |
| Off: The interface is not providing PoE power to any PD. |
Abundant Port Types
- Uplink port :Two 10GE optical ports.
- Service port: 24 GE ports, the last four are used with four optical ports as combo interfaces.
- Maintenance port:One RJ45 maintenance serial port; One RJ45 maintenance Ethernet port ; One mini USB maintenance serial port.
Large Capacity, High Performance, Integrated Design
- Integrated design: An AC can function as an access or aggregation device to provide wired access services and function as a management device to control STA access.
- Large switching capacity: An AC device has twenty-four GE interfaces and two 10GE interfaces. It provides 128 Gbit/s switching capacity and 10 Gbit/s forwarding capacity.
- PoE: The AC supports the PoE function and can provide the maximum power on 24 ports. This PoE capability can provide power to APs and other powered devices (PDs) connected to the AC unit.
Carrier-Class Reliability
- The AC supports port backup based on the Link Aggregation Control Protocol (LACP) or Multiple Spanning Tree Protocol (MSTP).
- The AC supports redundant AC/DC power supplies.
- The AC supports hot swappable power supplies.
- The AC supports 1+1 hot backup.
Easy-to-Install and Easy-to-Maintain
- The AC6605 dimensions (width x depth x height) are 442 mm × 420 mm × 44.4 mm and the AC6605 can be installed in a standard IEC cabinet (19 inch).
- Power supplies of AC are hot swappable, facilitating maintenance.
- The built-in web system of AC allows local GUI-based management.
- The AC can be managed by the eSight that provides various northbound interfaces.
- The AC support the intra-board temperature probe, which monitors the operating environment of the AC in real time.
Energy Conservation
- Low noise fans that can adjust the speed automatically are used, thus reducing noises in the system and power consumption of fans.
- The chip switches to the power saving mode when no connected device is detected on a service interface, that is, the interface is idle.
- It uses highly-integrated and energy-saving chips produced through advanced processing techniques. With the help of the intelligent device management system, the chips not only improve system performance but also greatly reduce power consumption of the entire system.
Switching and forwarding features
| Feature | Description | |
|---|---|---|
| Ethernet features | Ethernet | Operating modes of full duplex, half duplex, and auto-negotiation Rates of an Ethernet interface: 10 Mbit/s, 100 Mbit/s, 1000 Mbit/s, and auto-negotiation Flow control on interfaces Jumbo frames Link aggregation Load balancing among links of a trunk Interface isolation and forwarding restriction Broadcast storm suppression |
| VLAN | Access modes of access, trunk, hybrid, and Default VLAN | |
| MAC | Automatic learning and aging of MAC addresses Static, dynamic, and blackhole MAC address entries Packet filtering based on source MAC addresses Interface-based MAC learning limiting | |
| ARP | Static and dynamic ARP entries ARP in a VLAN Aging of ARP entries | |
| LLDP | LLDP | |
| Ethernet loop protection | MSTP | STP RSTP MSTP BPDU protection, root protection, and loop protection Partitioned STP |
IPv4 forwarding |
IPv4 features |
ARP and RARP ARP proxy Auto-detection NAT Bonjour Protocol |
| Unicast routing features | Static route RIP-1 and RIP-2 OSPF BGP IS-IS Routing policies and policy-based routing URPF check DHCP client, server and relay DHCP snooping | |
| Multicast routing features | IGMPv1, IGMPv2, and IGMPv3 PIM-SM Multicast routing policies RPF | |
IPv6 forwarding |
IPv6 features |
ND Protocol |
| Unicast routing features | Static route RIPng OSPFv3 BGP4+ IS-IS IPv6 DHCPv6 DHCPv6 Snooping | |
| Multicast routing features | MLD MLD Snooping | |
| Device reliability | BFD | BFD |
| Layer 2 multicast features | Layer 2 multicast | IGMP snooping Prompt leave Multicast traffic control Inter-VLAN multicast replication |
| Ethernet OAM | EFM OAM | Neighbor discovery Link monitoring Fault notification Remote loopback |
| QoS features | Traffic classification | Traffic classification based on the combination of the L2 protocol header, IP 5-tuple, outbound interface, and 802.1p priority |
| Action | Access control after traffic classification Traffic policing based on traffic classification Re-marking packets based on traffic classifiers Class-based packet queuing Associating traffic classifiers with traffic behaviors | |
| Queue scheduling | PQ scheduling DRR scheduling PQ+DRR scheduling WRR scheduling PQ+WRR scheduling | |
| Congestion avoidance | SRED WRED | |
| Configuration and maintenance | Terminal service | Configurations using command lines
Error message and help information in English Login through console and Telnet terminals Send function and data communications between terminal users |
| File system | File systems Directory and file management File uploading and downloading using FTP and TFTP | |
| Debugging and maintenance | Unified management over logs, alarms, and debugging information Electronic labels User operation logs Detailed debugging information for network fault diagnosis Network test tools such as traceroute and ping commands Interface mirroring and flow mirroring | |
| Version upgrade | Device software loading and online software loading BootROM online upgrade In-service patching | |
| Security and management | System security | Different user levels for commands, preventing unauthorized users from accessing AC SSHv2.0 RADIUS and HWTACACS authentication for login users ACL filtering DHCP packet filtering (with the Option 82 field) Defense against control packet attacks Defenses against attacks such as source address spoofing, Land, SYN flood (TCP SYN), Smurf, ping flood (ICMP echo), Teardrop, and Ping of Death attacks IPSec |
| Network management | ICMP-based ping and traceroute SNMPv1, SNMPv2c, and SNMPv3 Standard MIB RMON | |
AP Management Specifications
| Feature | Specifications |
|---|---|
| AP access control | Displays MAC addresses or SNs of APs in the whitelist. Adds a single AP or multiple APs (by specifying a range of MAC addresses or SNs) to the whitelist. Automatically discovering and manually confirming APs. Automatically discovering APs without manually confirming them. |
| AP region management | Supports three AP region deployment modes: ·Distributed deployment: APs are deployed independently. An AP is equivalent to a region and does not interfere with other APs. APs work at the maximum power and do not perform radio calibration. ·Common deployment: APs are loosely deployed. The transmit power of each radio is less than 50% of the maximum transmit power. ·Centralized deployment: APs are densely deployed. The transmit power of each radio is less than 25% of the maximum transmit power. Specifies the default region to which automatically discovered APs are added. |
| AP profile management | Specifies the default AP profile that is applied to automatically discovered APs. |
| AP type management | Manages AP attributes including the number of interfaces, AP types, number of radios, radio types, maximum number of virtual access points (VAPs), maximum number of associated users, and radio gain (for APs deployed indoors). Provides default AP types. Supports user-defined AP types. |
| Network topology management | Supports LLDP topology detection. |
Radio Management Specifications
| Feature | Specifications |
|---|---|
Radio profile management |
The following parameters can be configured in a radio profile: Radio working mode and rate |
| Unified static configuration of parameters | Radio parameters such as the channel and power of each radio are configured on the AC and then delivered to APs. |
| Dynamic management | APs can automatically select working channels and power when they go online. In an AP region, APs automatically adjust working channels and power in the event of signal interference: ·Global calibration: The optimal working channel and power of a specified AP can be adjusted. ·Partial calibration: The optimal working channels and power of all the APs in a specified region can be adjusted. When an AP is removed or goes offline, the AC6605-26-PWR increases the power of neighboring APs to compensate for the coverage hole. Automatic selection and calibration of radio parameters in AP regions are supported. |
Enhanced service capabilities |
The AC supports 802.1a/b/g/n/ac. These modes can be used independently or jointly (a\n, b\g, b\g\n, and g\n). |
WLAN Service Management Specifications
| Feature | Specifications |
|---|---|
| ESS management | Allows you to enable SSID broadcast, set the maximum number of access users, and set the association aging time in an ESS. Isolates APs at Layer 2 in an ESS. Maps an ESS to a service VLAN. Associates an ESS with a security profile or a QoS profile. Enables IGMP for APs in an ESS. |
| VAP-based service management | Adds multiple VAPs at a time by binding radios to ESSs. Displays information about a single VAP, VAPs with a specified ESS, or all VAPs. Supports configuration of offline APs. Creates VAPs according to batch delivered service provisioning rules in automatic AP discovery mode. |
| Service provisioning management | Supports service provisioning rules configured for a specified radio of a specified AP type. Adds automatically discovered APs to the default AP region. The default AP region is configurable. Applies a service provisioning rule to a region to enable APs in the region to go online. |
| Multicast service management | Supports IGMP snooping. Supports IGMP proxy. |
| Load balancing | Performs load balancing among radios in a load balancing group. Supports two load balancing modes: Based on the number of STAs connected to each radio Based on the traffic volume on each radio |
| BYOD (Bring Your Own Device) | Identification of device types according to the OUI in the MAC address Identification of device types according to the user agent (UA) field in an HTTP packet Identification of device types according to DHCP Option information Carrying of device type information in RADIUS authentication and accounting packets |
| Positioning services | Locating AeroScout and Ekahau tags Locating Wi-Fi terminals |
| Spectrum analysis | Identification of the following interference sources: bluetooth, microwave ovens, cordless phones, ZigBee, game controller, 2.4 GHz/5 GHz wireless audio and video devices, and baby monitors. Working with the eSight to locate the interference sources and display spectrum. |
QOS
| Feature | Specifications |
|---|---|
| WMM profile management | Enables or disables Wi-Fi Multimedia (WMM). Allows a WMM profile to be applied to radios of multiple APs. |
| Traffic profile management | Manages traffic from APs and maps packet priorities according to traffic profiles. Applies a QoS policy to each ESS by binding a traffic profile to each ESS. |
| AC traffic control | Manages QoS profiles. Uses ACLs to perform traffic classification. Limits incoming and outgoing traffic rates for each user based on inbound and outbound CAR parameters. Limits the traffic rate based on ESSs or VAPs. |
| AP traffic control | Controls traffic of multiple users and allows users to share bandwidth. Limits the rate of a specified VAP. |
| Packet priority configuration | Sets the QoS priority (IP precedence or DSCP priority) for CAPWAP control channels. Sets the QoS priority for CAPWAP data channels: Allows you to specify the CAPWAP header priority. Maps 802.1p priorities of user packets to ToS priorities of tunnel packets. |
Airtime scheduling |
Allocates equal time to users for occupying the channel, which improves users' Internet access experience. |
WLAN Security Specifications
| Feature | Specifications |
|---|---|
| WLAN security profile management | Manages authentication and encryption modes using WLAN security profiles. Binds security profiles to ESS profiles. |
| Authentication modes | Open system authentication with no encryption WEP authentication/encryption WPA/WPA2 authentication and encryption: WPA/WPA2-PSK+TKIP WPA/WPA2-PSK+CCMP WPA/WPA2-802.1x+TKIP WPA/WPA2-802.1x+CCMP WAPI authentication and encryption: Supports centralized WAPI authentication. Supports three-certificate WAPI authentication, which is compatible with traditional two-certificate authentication. Issues a certificate file together with a private key. Allows users to use MAC addresses as accounts for authentication by the RADIUS server. Portal authentication: Allows an AC to function as a portal gateway. Prohibits an AC from functioning as a portal gateway. Supports only Layer 2 portal. |
| Combined authentication | Combined MAC authentication: PSK+MAC authentication MAC+portal authentication: MAC authentication is used first. When MAC authentication fails, portal authentication is used. This type of authentication applies only to centralized forwarding. |
| AAA | Local authentication/local accounts (MAC addresses and accounts) RADIUS authentication Multiple authentication servers: Supports backup authentication servers. Specifies authentication servers based on account. Configures authentication servers based on account. Binds user accounts to SSIDs. |
| Security isolation | Port-based isolation User group-based isolation |
| WIDS | Rouge device scan, identification, defense, and countermeasures, which includes dynamic blacklist configuration and detection of rogue APs, STAs, and network attacks. |
| Authority control | ACL limit based on the following: Port User group User |
| Other security features | SSID hiding IP source guard: Configures IP and MAC binding entries statically. Generates IP and MAC binding entries dynamically. |
WLAN user management specifications
| Feature | Specifications |
|---|---|
| Address allocation of wireless users | Functions as a DHCP server to assign IP addresses to wireless users. |
| WLAN user management | Supports user blacklist and whitelist. Controls the number of access users: Based on APs Based on SSIDs Logs out users in any of the following ways: Using RADIUS DM messages Using commands Supports various methods to view information: Allows you to view the user status by specifying the user MAC address, AP ID, radio ID, or WLAN ID. Displays the number of online users in an ESS, AP, or radio. Collects packet statistics on air interface based on user. |
| WLAN user roaming | Supports intra-AC Layer 2 roaming. Supports inter-VLAN Layer 3 roaming on an AC. Supports fast key negotiation in 802.1x authentication. Authenticates users who request to reassociate with the AC and rejects the requests of unauthorized users. Delays clearing user information after a user goes offline so that the user can rapidly go online again. |
| User group management | Supports ACLs. Supports user isolation: Inter-group isolation Intra-group isolation |
Management and Maintenance Features
Physical Specifications
| Item | Description | |
|---|---|---|
| Dimensions (width x depth x height) | 442 mm x 420 mm x 44.4 mm | |
| Maximum power consumption | 85 W | |
| Weight | Net weight: 5.48 kg Fully configured with 150 W power supplies: 7.16 kg Fully configured with 500 W power supplies: 7.48 kg | |
| Operating temperature | -5ºC to +50ºC | |
| Relative humidity | 5% RH to 95% RH, noncondensing | |
| Operating altitude | 150 W DC power supply: 0 m to 2000 m Others: 0 m to 3000 m | |
| AC input voltage | Rated voltage | 100 V AC to 240 V AC, 50/60 Hz |
| Voltage range | 90 V AC to 264 V AC, 47 Hz to 63 Hz | |
| DC input voltage | Rated voltage | -48 V DC to -60 V DC |
| Voltage range | -36 V DC to -72 V DC | |
System Configuration
| Item | Specifications |
|---|---|
| Processor | Dominant frequency: 1 GHz |
| Switching capacity | 128 Gbit/s |
| Forwarding capacity | 10 Gbit/s |
| DDR memory | 4 GB |
| Flash memory | 256 MB |
Protocol and Management Capabilities
| Parameter | Specifications |
|---|---|
| Number of managed APs | 1024 |
| Number of access users | Entire device: 10K Single AP: a maximum of 256 (depending on the AP model) |
| Number of MAC address entries | 16K |
| Number of VLANs | 4K |
| Number of routing entries | 10K |
| Number of ARP entries | 8K |
| Number of multicast forwarding entries | 4K |
| Number of DHCP IP address pools | 128 IP address pools, each of which contains a maximum of 16K IP addresses |
| Number of local users | 1000 |
| Number of ACLs | 8K |
| Number of ESSIDs | 4K |
| User group management | 128 user groups Each user group can reference a maximum of eight ACLs. Each user group can associate with a maximum of 128 ACL rules. |
Wireless Networking Capabilities
| Feature | Specifications |
|---|---|
| Networking between APs and ACs | APs and ACs can be connected through a Layer 2 or Layer 3 network. APs can be directly connected to an AC. APs are deployed on a private network, while ACs are deployed on the public network to implement NAT traversal. ACs can be used for Layer 2 bridge forwarding or Layer 3 routing. |
| Forwarding mode | Direct forwarding (distributed forwarding or local forwarding) Tunnel forwarding (centralized forwarding) Centralized authentication and distributed forwarding Before users are authenticated, tunnel forwarding is used. After users are authenticated, local forwarding is used. |
| Wireless networking mode | WDS bridging: Point-to-point (P2P) wireless bridging Point-to-multipoint (P2MP) wireless bridging Automatic topology detection and loop prevention (STP) Wireless mesh network Access authentication for mesh devices Mesh routing algorithm Go-online without configuration |
AC discovery |
An AP can obtain the device's IP address in any of the following ways: Static configuration DHCP DNS The AC uses DHCP or DHCPv6 to allocate IP addresses to APs. DHCP or DHCPv6 relay is supported. On a Layer 2 network, APs can discover the AC by sending broadcast CAPWAP packets. |
CAPWAP tunnel |
Centralized CAPWAP CAPWAP control tunnel and data tunnel (optional) CAPWAP tunnel forwarding and direct forwarding in an extended service set (ESS) Datagram Transport Layer Security (DTLS) encryption Heartbeat detection and tunnel reconnection |
Active and standby ACs |
Enables and disables the switchback function. |
Application Scenarios
The AC6605-26-PWR is connected to an aggregation switch in chain or branched mode.
The AC6605-26-PWR processes both control flows and data flows. Management flows must be transmitted over Control And Provisioning of Wireless Access Points (CAPWAP) tunnels. Data flows can be transmitted over CAPWAP tunnels or not, as required.
The CAPWAP protocol defines how APs communicate with ACs and provides a general encapsulation and transmission mechanism for communication between APs and ACs. CAPWAP defines data tunnels and control tunnels.
Data tunnels encapsulate 802.11 data packets to be sent to the AC.
Control tunnels transmit control flows for remote AP configuration and WLAN management.
Two forwarding modes are available according to whether data flows are transmitted on CAPWAP tunnels:
Direct forwarding: is also called local or distributed forwarding.
Tunnel forwarding: is also called centralized forwarding. It is usually used to control wireless user traffic in a centralized manner.
You can select the chain or branched mode according to networking requirements. On the AC, you can configure direct forwarding for some APs and tunnel forwarding for other APs. In tunnel forwarding mode, all wireless user traffic is aggregated to an AC, which may create a switching bottleneck. Therefore, tunnel forwarding is seldom used on enterprise networks.
Chain Networking
In chain networking mode, APs or access switches are directly connected to the AC. The AC functions as both an AC and an aggregation switch to forward and process APs' data and management services.
In chain networking mode, the AC sets up CAPWAP tunnels with APs to configure and manage these APs over CAPWAP tunnels. Service data of wireless users can be forwarded between APs and the AC over CAPWAP data tunnels or be directly forwarded by APs.
In chain networking mode, direct forwarding is often used so that user service data can be forwarded on APs.
The AC functions as the DHCP server to allocate IP addresses to APs. APs obtain the IP address of the AC using the DNS function, DHCP Option 43 in DHCP packets, or Layer 2 discovery protocols, and then set up data tunnels with the AC.

In direct forwarding mode, only control flows are transmitted in CAPWAP tunnels, and data flows sent from APs are transparently transmitted to the upstream device by the AC, as shown in Figure. Data flows are identified by VLAN IDs.
When data flows are not transmitted in CAPWAP tunnels, configure management VLANs and data VLANs as follows:
On the AC and its upstream switches, configure an AC management VLAN to transmit control flows between the AC and the NMS.
On the switches between APs and the AC, configure AP management VLANs to transmit control flows between APs and the AC.
On all switches between APs and the BRAS, configure data VLANs to differentiate WLAN service flows.
The AC6605-26-PWR has a wired switching unit that provides powerful access, aggregation, and switching capabilities. In addition, the AC6605-26-PWR provides PoE+ power for 24 interfaces so that APs can directly connect to the AC. Direct forwarding is often used in chain networking mode. This networking mode simplifies the network architecture and applies to large-scale and centralized WLANs.
Branched Networking
In branched networking mode, the AC is connected to a network device (usually an aggregation switch) to manage APs.
The AC only manages APs. Management flows are transmitted in CAPWAP tunnels, and data flows are forwarded to the upper layer network by the aggregation switch and BRAS and do not pass through the AC.
Direct Forwarding
In direct forwarding mode, wireless user service data is translated from 802.3 packets into 802.11 packets, which are then forwarded by an uplink aggregation switch.
The branched networking mode is often used on enterprise networks. Wireless user service data does not need to be processed by an AC, eliminating the bandwidth bottleneck and facilitating the usage of existing security policies. Therefore, this networking mode is recommended.
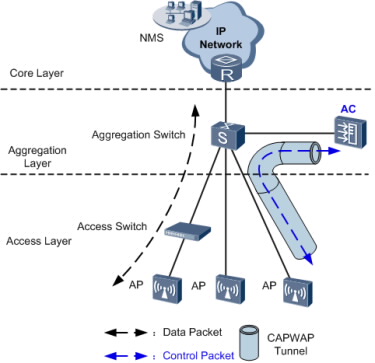
The AC only manages APs. All AP control flows must reach the AC.
The aggregation switch has a port to connect to the AC and functions as the DHCP server to allocate IP addresses to APs. APs obtain the IP address of the AC using the DNS function provided by the BRAS or DHCP Option 43 in DHCP packets.
Data flows from APs are forwarded by the Layer 2 switch, aggregation switch, and BRAS and do not pass through the AC.
Different VLANs are assigned to STAs with different service set identifiers (SSIDs). The Layer 2 switch and aggregation switch identify packets from these VLANs and forward these packets to the BRAS. The BRAS terminates packets from terminals, controls user access, and allocates IP addresses to users. After a user is authenticated by the BRAS, traffic from the user is forwarded to the Internet across the IP network.
Tunnel Forwarding
In tunnel forwarding mode, wireless user service data is transmitted between APs and ACs over CAPWAP tunnels.
In Figure, both management flows and data flows of APs are transmitted to the AC over CAPWAP tunnels, and then the AC transparently transmits these flows to the upstream device.
Tunnel forwarding is usually used to control wireless user traffic in a centralized manner. This forwarding mode facilitates device deployment and controls all wireless user data flows by aggregating traffic of all wireless users connected to APs to an AC through CAPWAP data tunnels.
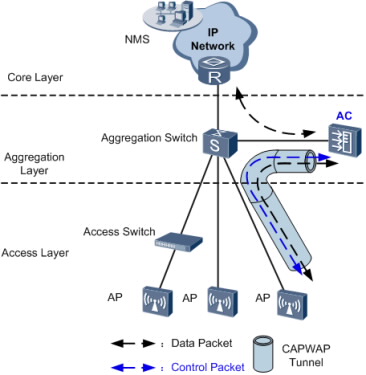
In branched networking mode, the AC manages all the APs connected to the aggregation switch. This network topology applies to scenarios where APs are scattered across hot spots.
The branched networking mode requires only a small modification to the existing network, facilitating device deployment. You can select the direct forwarding or tunnel forwarding mode according to networking requirements. Direct forwarding is recommended to enterprise networks.
Wireless Backhaul Networking
The 802.11 wireless technology has been widely used in home networks and enterprise networks. Users can easily access the Internet over WLANs. In this network application, APs must be connected to the existing wired network to provide network access services for wireless users. To expand the wireless coverage area, APs need to be connected using cables, switches, and power supplies. This increases network costs and prolongs network construction period. Wired deployment requirements may not be met in special circumstances. The Wireless Distribution System (WDS) or Wireless Mesh Network allows APs to be connected wirelessly, facilitating WLAN construction in a complex environment.
WDS
The WDS is a distribution system comprised of APs. The WDS connects to an AC on the network side, which is then connected to a network device such as a gateway or an aggregation switch. The WDS connects to a station (STA) or PC on the user side.
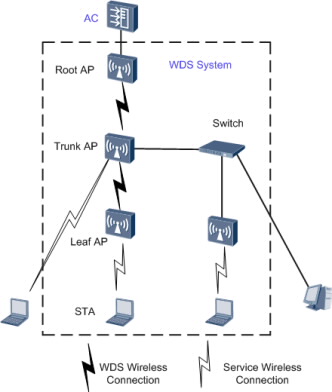
On a WDS network, an AC manages the following devices:
Root AP: connects to an AC on the wired side, and functions as a WDS master to connect to trunk APs or leaf APs.
Trunk AP: functions as a WDS slave to connect to a root AP, connects to wired devices on the wired side, or functions as a WDS master to connect to leaf APs.
Leaf AP: functions as a WDS slave to connect to a root AP or trunk AP or connects to STAs on the wireless side.
The WDS networking can expand WLANs and applies to indoor wireless deployment scenarios.
Wireless Mesh Network
Compared with a traditional WLAN, a wireless mesh network (WMN) has the following advantages:
Fast deployment: Mesh nodes can be easily installed to construct a WMN in a short time, much shorter than the construction period of a traditional WLAN.
Dynamic coverage area expansion: As more mesh nodes are deployed on a WMN, the WMN coverage area can be rapidly expanded.
Robustness: A WMN is a peer-to-peer network that will not be affected by the failure of a single node. If a node fails, packets are forwarded to the destination node along other paths.
Flexible networking: An AP can join or leave a WMN easily, allowing for flexible networking.
Various application scenarios: Besides traditional WLAN scenarios such as enterprise networks, office networks, and campus networks, a WMN also applies to scenarios such as large-scale warehouses, docks, MANs, metro lines, and emergency communications.
Cost-effectiveness: Only MPPs need to connect to a wired network, which minimizes the dependency of a WMN on wired devices and saves costs in wired device purchasing and cable deployment.
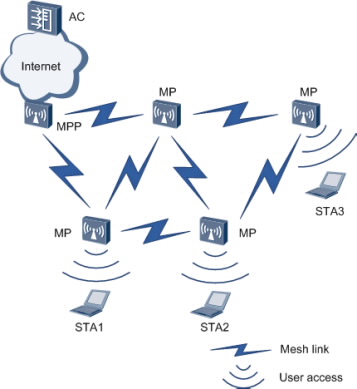
Nodes on a WMN can be classified into the following types based on their functions:
Mesh point (MP)
A mesh-capable node that uses IEEE 802.11 MAC and physical layer protocols for wireless communication. This node supports automatic topology discovery, automatic route discovery, and data packet forwarding.
Mesh portal point (MPP)
An MP that connects to a WMN or another type of network. This node has the portal function and enables mesh nodes to communicate with external networks.
On a WMN, MPs are fully meshed to establish an auto-configured, and self-healing backbone WMN, and MPPs with the gateway function provide connections to the Internet. An MP provides access services and connects a terminal to a WMN. A WMN uses special mesh routing protocols, which ensures high transmission quality. The WMN is applicable to scenarios that require high-bandwidth and highly-stable Internet connections.
Dual-AC Networking
To ensure uninterrupted service forwarding, enterprises that require high reliability use active and standby ACs for networking.
Dual-AC backup can be implemented in two modes:
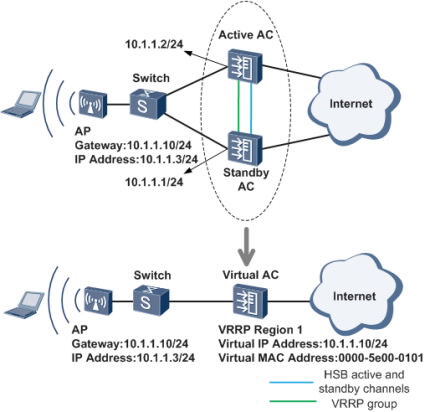
HSB + dual-link backup: an AP establishes CAPWAP tunnels with both the active and standby ACs. The two ACs synchronize service information (such as NAC and WLAN service information) through the hot standby (HSB) function. When an AP is disconnected from the active AC, the AP notifies the standby AC of a switchover.
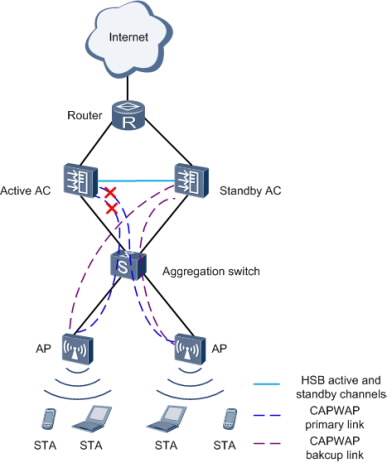
HSB + VRRP: an AP obtains only the virtual IP address of both the active and standby ACs. The active AC backs up information including AP entries, CAPWAP link information, and user information on the standby AC. In this mode, the AP only detects the presence of one AC. The active/standby switchover is determined by the Virtual Router Redundancy Protocol (VRRP). Currently, this mode cannot be used in a VRRP multi-instance scenario.