Sistema de defensa DDoS de la serie AntiDDoS8000
Los productos de la serie AntiDDoS8000 están diseñados para operadoras, empresas, centros de datos y proveedores de servicios ICP para implementar la defensa contra ataques a la capa de aplicaciones, ataques IPv4-IPv6, zombis, troyanos y gusanos. La serie garantiza de manera absoluta la seguridad de la red y la ininterrupción del servicio.
During the era of mobile Internet and Big Data, DDoS attacks become increasingly complex.
1. The peak attack traffic keeps growing. In 2013, the peak DDoS attack traffic exceeds 300 Gbit/s..
2. An increasing number of application-layer DDoS attacks occur in data center service systems..
3. The number of mobile service-specific DDoS attacks that come from mobile terminals increases rapidly.
4. Data centers are attack targets, and hackers can easily use a data center to launch attacks to external service systems.
Traditional anti-DDoS solutions in the industry cannot adapt to these changes.
Huawei Next Generation (NG) Anti-DDoS Solution performs abstract modeling and reputation system construction on network traffic from over 60 dimensions by leveraging Big Data analytics technologies. Compared to traditional anti-DDoS mechanisms in the industry, the Huawei NG Anti-DDoS Solution provides more precise and comprehensive DDoS attack defense.
Related Products
| Picture | Models |
|---|---|
|
AntiDDoS8030 has three expansion slots |
|
AntiDDoS8080 has eight expansion slots |
|
AntiDDoS8160 has 16 expansion slots |
Anti-Large-DDoS: Heavy Traffic DDoS Attack Defense
- Multi-core, distributed hardware architecture and Big Data-based Intelligent Defense Engine1 provide T-bit defense performance.
- Instant attack response within seconds protects link availability.
Anti-App-DDoS: Application DDoS Attack Defense
- Performs all traffic collection and 3-7-layer packet-by-packet analysis, create traffics models from over 60 dimensions, and provides the most precise and comprehensive attack detection.
- Fine-grained reputation system consisting of local session behavior-based reputation, service access behavior-based reputation, geographical location based reputation, and botnet cloud-based reputation precisely guards against various lightweight, slow application-layer DDoS attacks launched by botnets.
- Full-scale defense against over 100 attacks guarantees continuous operations of key service systems that encompass enterprise web applications and DNS, DHCP, and VoIP services.
Anti-Mobile-DDoS: Mobile DDoS Attack Defense
- Dynamic, real-time upgrade of 20,000 fingerprints and filtering of traffic by a mobile botnet database effectively defend DDoS attacks launched by botnets and mobile terminals and guarantees authorized access to mobile gateways.
- Protects availability of mobile data service systems such as mobile payment, mobile store, mobile social networking, and mobile game.
Anti-Outbound-DDoS: Inbound-to-Outbound DDoS Attack Defense
- Blocks the global most active zombie, Trojan horse, and worm controlling traffic.
- Blocks C&C DNS request traffic.
- Prevents DDoS attacks at the source.
Managed-Anti-DDoS: Managed DDoS Attack Defense Service
- Provides Zone (VIP)/service-based automatic and manual defense policies and complete defense methods.
- VIP/service-based independent statistics reports and email sending simplify defense management.
- Increases VIP' service stickiness by providing Portal-based self-service functions for VIP.
- Supports large-scale operations, for example, 10,000 VIPs/services, and protects 10,000 IP addresses of each VIP/service simultaneously.
| Attack Defense Functions (IPv4/IPv6 Supported) | ||
|---|---|---|
| Protocol abuse attack defense Defense against IP spoofing, LAND, Fraggle, Smurf, Winnuke, Ping of Death, Tear Drop, IP Option, IP Fragment Control Packet, TCP Label Validity Check, Large ICMP Control Packet, ICMP Redirect Control Packet, and ICMP Unreachable Control Packet attacks |
Web attack defense Defense against HTTP Get Flood, HTTP Post Flood, HTTP Head Flood, HTTP slow header flood, HTTP Slow Post Flood, HTTPS Flood, and SSL DoS/DDoS attacks | |
| Scanning and sniffing attack defense Defense against Port Scanning, IP Scanning, Tracert Control Packet, IP Option, IP Timestamp, and IP Routing Record attacks |
DNS attack defense Defense against DNS Query Flood attacks from real or spoofed source IP addresses, DNS Reply Flood attacks, DNS Cache Poisoning attacks, DNS Protocol Vulnerability Exploits, and DNS Reflection attacks | |
| Network-layer attack defense Defense against SYN Flood, ACK Flood, SYN-ACK Flood, FIN/RST Flood, TCP Fragment Flood, UDP Flood, UDP Fragment Flood, NTP Flood, ICMP Flood, TCP Connection Flood, Sockstress, TCP Retransmission, and TCP Null Connection attacks |
SIP attack defense Defense against SIP methods Flood attacks | |
| DHCP attack defense Defense against DHCP Flood attacks | ||
| Mobile attack defense Defensible DDoS attacks launched by mobile botnets, for example, AnDOSid/WebLOIC/Android.DDoS.1.origin | ||
| Zombie, Trojan horse, worm and tools traffic blocking: Blocking of controlling traffic of active zombies, Trojan horses, worms, and tools, such as LOIC, HOIC, Slowloris, Pyloris, HttpDosTool, Slowhttptest,Thc-ssl-dos, YoyoDDOS, IMDDOS, Puppet, Storm, fengyun, AladinDDoS, And so on C&C DNS request traffic blocking |
Feature-based filtering Blacklist, HTTP/DNS/SIP/DHCP field-based filtering, and IP/TCP/UDP/ICMP/Other Protocol field-based and load feature-based filtering | |
| IP reputation database 12 data centers across the globe process 12 billion query analysis requests on a daily basis and tracks the global most active 5 million zombie hosts with a daily update. | ||
| Management and reports | ||
| Supports account management and rights allocation; supports 10,000 defense objects; supports import of defense policies in batches; supports device performance monitoring; supports source tracking through packet capture and fingerprint extraction; supports SMS/Voice/Email alarming; supports log dumping; supports network traffic model learning, supports multidimensional reports including attack traffic analysis, attack event analysis, and attack trend analysis; supports download of reports in multiple formats such as HTML, PDF, Excel, and CSV; supports report push through emails; and supports Portal-based operations. | ||
| Networking and Traffic Diversion Policies | ||
| Deployment Modes: Supports inline and bypass deployment. | Traffic Diversion Policies: Supports manual traffic diversion and multiple automatic traffic diversion modes such as policy-based routing and BGP routing. | |
| Interface and Hardware Parameters | ||||
|---|---|---|---|---|
| AntiDDoS8030 | AntiDDoS8080 | AntiDDoS8160 | ||
| Max Performance | 40Gbps/80Gbps | 100Gbps/480Gbps | 200Gbps/960Gbps | |
| Max Performance/Slot | 20Gbps | 20Gbps | 20Gbps | |
| 80Gbps | 160Gbps | 160Gbps | ||
| Expansion slot | 3 | 8 | 16 | |
| Interface Card Type | LPUF-21 interface card | 12 x 1GE (RJ45)/12 x 1GE (SFP)/1 x 10GE (XFP)/4 x 10GE (XFP)/1 x 10GE POS (XFP) | ||
| LPUF-40 interface card | 20 x 1GE (SFP)/2 x 10GE (XFP)/4 x 10GE (XFP) | |||
| LPUF-101 interface card | 24 x GE (SPF)/4 x 10GE (SPF+)/5 x 10GE (SPF+)/1 x 40GE (CPF)/1 x 100GE (CPF) | |||
| Reliability | Supports dual MPUs and achieves a five-nine carrier-grade reliability (99.999%). | |||
| Power Supply Type | Supports both DC and AC power supply. | |||
Comments:
1. IP reputation database Function will be ready in 2014Q4
2. AntiDDoS8030 with SPUC max performance can get 80Gbps, and SPUC will be ready in 2014Q4
3. AntiDDoS8080/8160 with SPUD max performance can get 480Gbp/960Gbps and SPUD will be ready in 2014Q4
IDC Secure and Profitable Operation
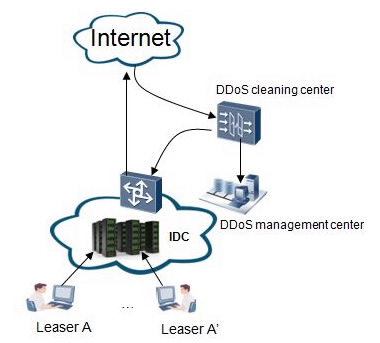
HUAWEI Anti-DDoS solution deployed at the IDC egress delivers the following functions:
1. Defends against attacks on the DNS server, for example, DNS protocol stack vulnerability attacks, DNS reflection attacks, DNS flood attacks, and DNS Cache-Miss attacks, and supports DNS cache for improved DNS server performance under heavy traffic
2. Defends against attacks on Web servers, for example, SYN flood attacks, HTTP flood attacks, CC attacks, and low-rate connection attacks.
3. Defends against attacks on online games, for example, UDP flood attacks, SYN flood attacks, and TCP attacks.
4. Defends against SSL DoS/DDoS attacks on HTTPS servers.
5. Provides customers with self-service policy configuration and report by operating Anti-DDoS as a security service.
| AntiDDoS8030 | ||
|---|---|---|
| AntiDDoS8030-BASE-DC | AntiDDoS8030 DC Basic Configuration(include X3 DC Chassis,2*MPU),with HS General Security Platform Software | Alternative |
| AntiDDoS8030-BASE-AC | AntiDDoS8030 DC Basic Configuration(include X3 DC Chassis,2*MPU),with HS General Security Platform Software | |
| AntiDDoS8080 | ||
| AntiDDoS8080-BASE-DC | AntiDDoS8080 DC Basic Configuration(include X8 DC Chassis,2*SRU,1*SFU),with HS General Security Platform Software | Mandatory |
| CR52-PWRA-AC-DF | AC Distribution Frame for Cabinet,2 or 6 Input,6(2*3) Output,6 Group of 2 Poles 20A Air Switch | AC mandatory |
| USG9500-PWR-AC | AC Power Supply Module | AC mandatory |
| AntiDDoS8160 | ||
| AntiDDoS8160-BASE-DC | AntiDDoS8160 DC Basic Configuration(include X16 DC Chassis,2*MPU,4*SFU),with HS General Security Platform Software | Mandatory |
| CR52-PWRA-AC-DF | AC Distribution Frame for Cabinet,2 or 6 Input,6(2*3) Output,6 Group of 2 Poles 20A Air Switch | AC mandatory |
| USG9500-PWR-AC | AC Power Supply Module | AC mandatory |
| SPU of the AntiDDoS 8000 series | ||
| ADS-SPUA01 | Service Processing Unit, Double CPUs, with HS General Security Platform Software | Optional (the SPU must be used with a license) |
| LIC-ADS-10GDDD00 | Capability for Detector(a multiple of 10G),with HS General Security Platform Software | |
| LIC-ADS-10GDDC00 | Capability for Cleaning (a multiple of 10G),with HS General Security Platform Software | |
| ADS-SPUA02 | Service Processing Unit, Four CPUs, with HS General Security Platform Software | Optional (the SPU must be used with a license) |
| LIC-ADS-20GDDD00 | Capability for Detector(a multiple of 20G),with HS General Security Platform Software | |
| LIC-ADS-20GDDC00 | Capability for Cleaning (a multiple of 20G),with HS General Security Platform Software | |
| LPU of the AntiDDoS 8000 series | ||
| LPUF40 | ||
| FWCD0LPUF40A01 | Flexible Card Line Processing Unit(LPUF-40,2 sub-slots) A, with HS General Security Platform Software | Optional |
| FWCD00L2XX01 | 2-Port 10GBase LAN/WAN-XFP Flexible Card(P40) | Optional |
| FWCD00EFGF01 | 20-Port 100/1000Base-X-SFP Flexible Card(P40) | Optional |
| LPUF21 | ||
| FWCD0LPUKD01 | Flexible Card Line Processing Unit(LPUF-21,2 Sub-Slots) B, with HS General Security Platform Software | Optional |
| FWCD00L1XX01 | 1-Port 10GBase WAN/LAN XFP Flexible Interface Daughter Card, with HS General Security Platform Software | Optional |
| FWCD00EBGF01 | 12-Port 100/1000Base-X SFP Flexible Interface Daughter Card, with HS General Security Platform Software | Optional |
| FWCD00EBGE01 | 12-Port 10/100/1000Base-TX RJ45 Flexible Interface Daughter Card, with HS General Security Platform Software | Optional |
| FWCD0P1XBZ01 | 1 Port OC-192c/STM-64c POS-XFP Flexible Card, with HS General Security Platform Software | Optional |
| Anti-DDoS components | ||
| ADSCT001WIN01 | Windows Chinese Platform(AC PC Server, Hard Disk, Microsoft Windows Server and Patches, Chinese), Including OS License | Optional |
| ADSCT001WIN03 | Windows Chinese Platform(DC PC Server, Hard Disk, Microsoft Windows Server and Patches, Chinese), including OS License | Optional |
| NS19MKM00 | KB&Mouse, Monitor 19-Inch TFT LCD | Optional |
| Anti-DDoS management center | ||
| LIC-ADS-NOFA00 | ATIC Basic Feature Summary ,with HS General Security Platform Software | Alternative |
| LIC-ADS-DOFA00 | ATIC Operation Feature Summary ,with HS General Security Platform Software (including professional DNS defense) | |
| Product customization and development expense | ||
| E8KE-EXTRAD01 | Extra Product Function Requirement Customized Development Fee-with HS General Security Platform Software | Optional |
| Professional Anti-DDoS defense | ||
| LIC-ADS-DNS00 | DNS Professional Protection Function ,with HS General Security Platform Software | Optional |
| LIC-ADS-WEB00 | Web Professional Protection Function ,with HS General Security Platform Software | Optional |
| LIC-ADS-DOM50 | Number of DDoS Zone(a multiple of 10),with HS General Security Platform Software | Optional |
| LIC-ADS-10GDDD00 | Capability for Detector(a multiple of 10G),with HS General Security Platform Software | Optional |
| LIC-ADS-10GDDC00 | Capability for Cleanning (a multiple of 10G),with HS General Security Platform Software | Optional |
| LIC-ADS-20GDDD00 | Capability for Detector(a multiple of 20G),with HS General Security Platform Software | Optional |
| LIC-ADS-20GDDC00 | Capability for Cleaning (a multiple of 20G),with HS General Security Platform Software | Optional |
| Subrack optical splitter | ||
| OOS314S00 | Optical Splitter ,Single Mode ,Support Three Optical Links(1*4 each),1310/1550nm,+/-40nm,70:10:10:10,LC/UPC,0.25mm,SMF-28e,180.3*144.45*18.1 | Optional |
| OOS412S00 | Optical Splitter ,Single Mode ,Support Four Optical Links(1*2 each),1310/1550nm,+/-40nm,80:20,LC/UPC,0.25mm,SMF-28e,0.2dB,180.3*144.45*18.1 | Optional |
| OOS413S00 | Optical Splitter ,Single Mode ,Support Four Optical Links(1*3 each),1310/1550nm,+/-40nm,70:15:15,LC/UPC,0.25mm,SMF-28e,180.3*144.45*18.1 | Optional |
| OOS412M00 | Optical Splitter ,Multi-mode ,Support Four Optical Links(1*2 each),850nm,+/-40nm,50:50,LC/UPC,0.25mm,62.5/125ume, 250um loose tube,0.2dB,180.3*144.45*18.1 | Optional |
| OOSSMRC00 | Optical Splitter ,Single Mode /Multi-mode ,Rack-mounted Optical Splitter Chassis(Used with Optical Splitter Cards),850/1310/1550nm,482.6*209*43.6mm | Optional |
| OOS412S01 | Optical Splitter ,Single Mode , Support Four Optical Links(1*2 each),1310/1550nm,+/-40nm,50:50,LC/UPC,0.25mm,SMF-28e,0.2dB,180.3*144.45*18.1mm | Optional |




